Zerodium, a company that buys exploits to sell to government agencies, is offering up to $1 million for zero-days affecting the Tor Browser.
In a bug acquisition program launched today, the company says it’s interested in Tor Browser exploits that “[lead] to remote code execution on the targeted OS either with privileges of the current user or with unrestricted root/SYSTEM privileges.”
The company said it’s searching for exploits that work on Tails — a privacy-hardened version of Linux — and Windows.
Zerodium wants no-user-interaction Tor Browser exploits
The exploit broker is interested in high-complexity exploits that do not require user interaction or show any errors or popups. Zerodium said it’s looking for zero-days that require users only to visit a web page.
The company is not picky, accepting zero-days that work against Tor Browser instances running with security settings set to “high” (JavaScript disabled) or security settings set to “low” (default Tor Browser configuration).
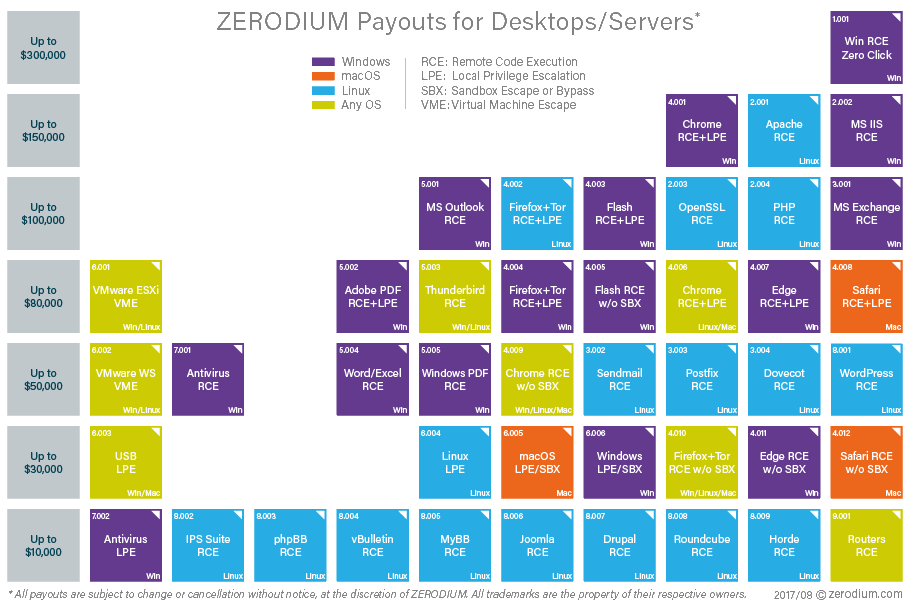
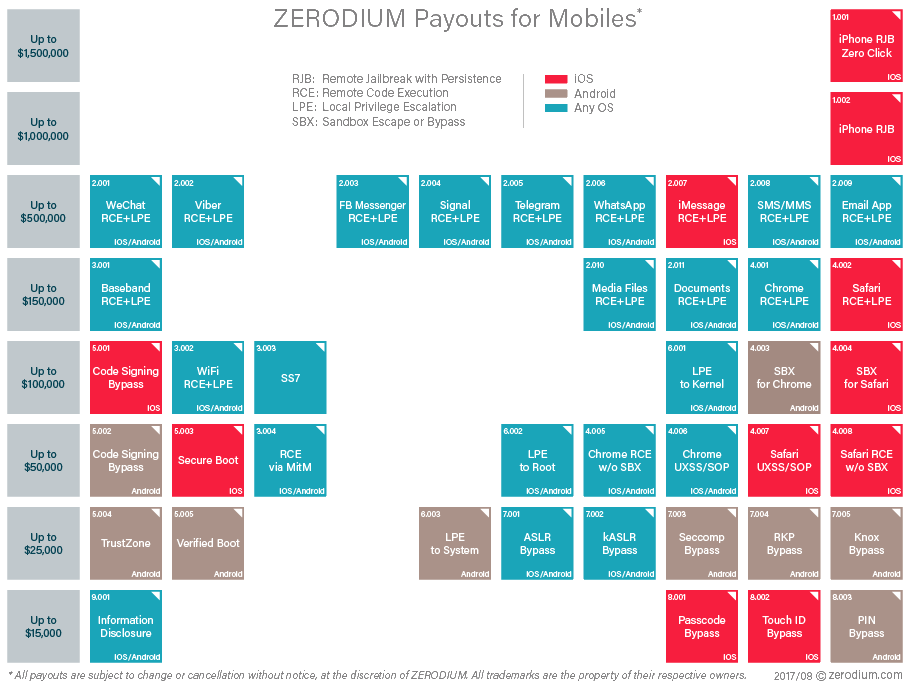
Zerodium has been running an exploit acquisition programs for years, and lists two price tables on its website, for desktop/server-related exploits, and for app/mobile-related zero-days.
|
|
The company was already willing to dish out a maximum of $100,000 per Tor Browser exploits, under normal circumstances.
The recently launched “Tor Browser Zero-Day Bounty” comes with special prices, above the previous price points.
| Software / OS | JavaScript Blocked (Security Settings: HIGH) | JavaScript Allowed (Default) (Security Settings: Low) | ||
| RCE+LPE to Root/SYSTEM | RCE Only (No LPE) | RCE+LPE to Root/SYSTEM | RCE Only (No LPE) | |
| Tor Browser on Tails 3.x (64bit) AND on Windows 10 RS3/RS2 (64bit) | $250,000 | $185,000 | $125,000 | $85,000 |
| Tor Browser on Tails 3.x (64bit) OR on Windows 10 RS3/RS2 (64bit) | $200,000 | $175,000 | $100,000 | $75,000 |
Governments looking for a way to deanonymize Tor users
In a FAQ section on its website, Zerodium says it launched this special Tor Browser zero-day acquisition program in response to government agencies looking for tools that deanonymize Tor users.
“The Tor network and browser are, in many cases, used by ugly people to conduct activities such as drug trafficking or child abuse,” Zerodium explains. “We have launched this special bounty for Tor Browser zero-days to help our government customers fight crime and make the world a better and safer place for all.”
As a result, the company has set aside a budget of $1,000,000 that it will use to pay zero-days submitted during this urgent run on Tor Browser exploits. Once the budget is exhausted, the company will revert to the old prices, which aren’t that small either, far above what official bug bounty programs pay out.
“The [Tor Browser] zero-day prices are very high,” said a Romanian bug bounty hunter who wanted to remain anonymous for this article. “But Tor is hard to crack. Getting RCE on Tails is almost impossible, imho. If I have that I’m selling the exploit for $1,000,000 easily on my own.”
Many security researchers usually stay away from companies like Zerodium on moral grounds. Exploit brokers like Zerodium, HackingTeam, or FinFisher buy exploits and assemble them into surveillance and spyware tools that often make their way into the hands of oppressive regimes that later use these tools to spy, hunt, and catch political adversaries, journalists, disidents, and others.
Last month, Zerodium updated its price chart to include fees for zero-days discovered in encrypted IM clients, such as Signal, WhatsApp, Telegram, Viber, iMessage, Facebook Messenger, or WeChat. Based on the exploit’s efficiency, the company was willing to pay up to $500,000 for such exploits. Encrypted IM apps have also become a favorite among both the criminal underground and dissidents and privacy-conscious users alike.
Image credits: Zerodium