
According to a new law voted in 2016 and which came into effect starting June 1, 2017, foreign companies activating in China could be forced to provide access to their source code to a state agency that has been recently linked to China’s nation-state cyber-espionage campaigns.
China’s new cyber-security law (CSL) gives the China Information Technology Evaluation Center (CNITSEC) the legal power to conduct “national security reviews” of foreign companies that want to activate on the Chinese market.
According to articles in the CSL, this also includes the power to request access to any app or service’s source code.
Chinese authorities say this is to protect citizens by searching the source code of foreign companies for secret mechanisms that collect data on Chinese users and send it to foreign servers.
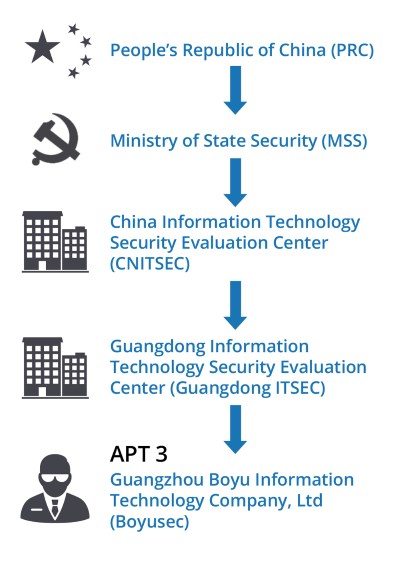
CNITSEC previously linked to APT3
The problem here is that a previous Recorded Future report has linked CNITSEC as the handler of Boyusec, a Chinese company linked to the activities of APT3, a cyber-espionage unit that was responsible for hacking companies in Hong Kong and the US [1, 2, 3, 4].
Experts believe that CNITSEC could use these mandatory source code audits to gather information on vulnerabilities in the analyzed apps.
Previous reports — and books — have detailed how Chinese authorities use state agencies to issue broad commands and provide support to a network of third-parties that perform the actual hacking on behalf of the Chinese state and feed back the stolen data back into the system.
This data later makes its way to Chinese companies as part of a well-oiled industrial espionage machine supported by the Chinese government itself. This same targeting and stolen data dissemination pattern was also detailed in a talk at the Troopers 2017 security conference by infosec expert The Grugq.
[embedded content]
Code audits could help Chinese hackers find security bugs
Experts fear that vulnerabilities found in the CNITSEC audits would make their way down this complex network and eventually be used against the foreign companies or their clients.
A Financial Times report published before the CSL went into effect revealed that many multinationals shared these fears and were wary of China’s new law, fearing it would leave them vulnerable to industrial espionage and give Chinese companies an unfair advantage.
Nonetheless, many won’t have a choice, as CSL will create an impossible choice for foreign companies, making them choose between giving their proprietary technology to CNITSEC or being pushed out of the Chinese IT market, which is projected to reach $242 billion in 2018.
Russia has a similar law
In a KPMG report published in February 2017 and in a Recorded Future report published yesterday, experts warn that the new CSL contains broad language that allows Chinese authorities to target even fast food services, not necessarily IT companies.
Broad laws like the CSL make it hard for foreign companies to trust the Chinese government.
In Russia, where the government has approved a similar law, companies like Cisco, IBM, and SAP have already agreed to provide the Russian government access to their source code.
For now, companies like Microsoft, Intel, IBM, and others have pushed back against the new CSL and the Chinese government last year, but with no success.
Most likely, tech giants will have no choice and will eventually have to comply if they don’t want to be cut out of the Chinese market, just like Google’s search engine was pushed out a few years back when it declined to honor various censorship requests.

