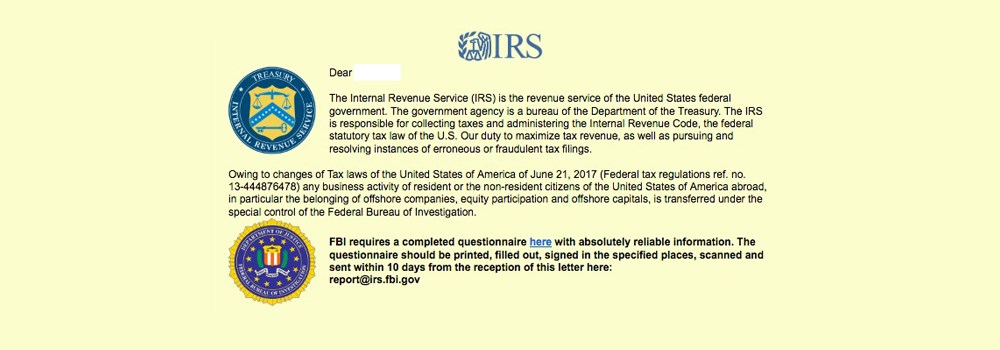
The Internal Revenue Service (IRS) is warning US citizens of a new phishing scheme that poses as official IRS communications in the hopes that victims access a link, download a file, and hopefully get infected with ransomware.
The email, pictured above, tries to convince users they need to download a questionnaire, print it, fill it with their personal details, scan it, and then send it to an IRS email address.
To look as realistic as possible, the phishing email also bears the logos of the IRS and the FBI.
In reality, this scam’s only purpose is to convince users to download a file that is laced with a yet unidentified form of ransomware that infects users’ PCs and encrypts their files.
People with tax issues won’t get their first contact via email
“This is a new twist on an old scheme,” said IRS Commissioner John Koskinen. “People should stay vigilant against email scams that try to impersonate the IRS and other agencies that try to lure you into clicking a link or opening an attachment.”
“People with a tax issue won’t get their first contact from the IRS with a threatening email or phone call,” Koskinen also added.
Yesterday’s IRS alert comes four weeks after the IRS issued a series of recommendations for dealing with ransomware attacks as part of its “Don’t Take the Bait” drive.
The “Don’t Take the Bait” campaign is a 10-week security awareness campaign aimed at tax professionals in the hopes of increasing awareness about various cyber threats.
Some of the recommendations included in this campaign are worth re-posting:
✬ Make sure employees are aware of ransomware and of their critical roles in protecting the organization’s data.
✬ For digital devices, ensure that security patches are installed on operating systems, software and firmware. This step may be made easier through a centralized patch management system.
✬ Ensure that antivirus and anti-malware solutions are set to automatically update and conduct regular scans.
✬ Manage the use of privileged accounts — no users should be assigned administrative access unless necessary, and only use administrator accounts when needed.
✬ Configure computer access controls, including file, directory and network share permissions, appropriately. If users require read-only information, do not provide them with write-access to those files or directories.
✬ Disable macro scripts from office files transmitted over e-mail.
✬ Implement software restriction policies or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers, compression/decompression programs.
✬ Back up data regularly and verify the integrity of those backups.
✬ Secure backup data. Make sure the backup device isn’t constantly connected to the computers and networks they are backing up. This will ensure the backup data remains unaffected by ransomware attempts.
The IRS also actively encourages users to send any IRS-themed phishing scams to phishing@irs.gov.

