Security researchers have discovered two flaws that affect the extension systems embedded in today’s browsers, such as Firefox, Safari, and all the Chromium-related offshoots, such as Chrome, Opera, and others.
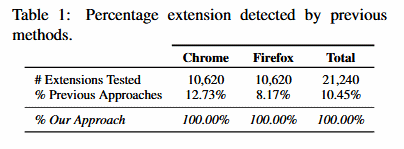
These flaws can be exploited by a determined attacker to expose a list of the user’s installed extensions with a 100% accuracy. This information can be used to fingerprint users based on their installed extensions, to unmask anonymous users hiding behind VPN or Tor traffic, or to create advertising profiles.
First flaw affects widely used WebExtensions API
Two researchers from the University of Deusto in Spain and a researcher from Eurecom, a French research center, have discovered these flaws.
The first flaw affects the extension system used with Chromium-based browsers such as Google Chrome, Opera, the Yandex Browser, and Comodo Dragon.
The same extension system — the WebExtensions API — is also used by newer versions of Firefox, Edge, Vivaldi, and Brave. Researchers didn’t test these browsers, but they said they believe them to be affected as well.
The WebExtensions API protects browsers against attackers trying to list installed extensions by using access control settings in the form of the manifest.json file included in every extension. This file blocks websites from checking any of the extension’s internal files and resources unless the manifest.json file is specifically configured to allow it.
Timing side-channel attack on WebExtensions add-ons
The research team says it discovered a “timing side-channel attack on access control settings validation.”
Researchers found that browser using the Chromium WebExtensions API take a little bit longer to reply to a request from a website for files stored locally for a bogus extension compared to a valid extension but with the wrong path.
chrome-extension://[fakeExtID]/[fakePath]
chrome-extension://[realExtID]/[fakePath]
This allowed researchers to deduce which extensions are installed in the user’s browser by bombarding the target with a series of dual requests and recording the time it takes a browser to respond.
This worked for Chrome, Opera, Yandex Browser, and Comodo Dragon.
Old Firefox add-on system also affected by the same flaw
Firefox is also vulnerable. The browser is currently transitioning from the old XML-based Add-ons API to the Chromium-friendly WebExtensions API.
Researchers didn’t test the newer implementation since it was still under development, but they said the old Add-ons API is also vulnerable to the same attack. Furthermore, because Firefox raises special errors for when requesting files from fake extensions, the attack is even more accurate on Firefox.
Safari affected by URL leakage
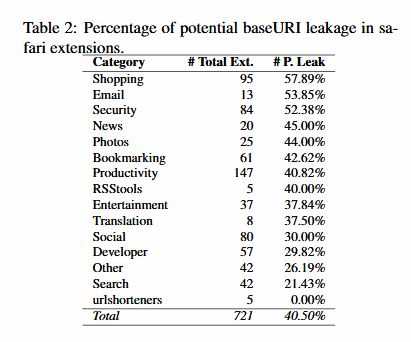
The second flaw they discovered is called URI leakage and affects Safari’s extensions model. These extensions don’t use manifest.json file to restrict access to extension files. Instead, they generate a random URL per browser session that only users can access while using the browser.
Researchers discovered methods to leak the data necessary to guess these random URLs. Tests showed they were able to leak the extension’s URL in 40.5% of tested extensions.
Flaws not fixed
“We responsibly disclosed all our findings and we are now discussing with the developers of several browsers and extensions to propose the correct countermeasures to mitigate these attacks in both current and future versions,” the research team says.
In their research paper — titled “Extension Breakdown: Security Analysis of Browsers Extension Resources Control Policies” — researchers also detailed methods of using these two flaws for advertising analytics purposes, but also for malicious applications such as targeted malware, social engineering, or vulnerable extension exploitation.
Image credits: Sergey Demushkin, Bleeping Computer

