Security researchers from Akamai, Cloudflare, Flashpoint, Google, Oracle Dyn, RiskIQ, Team Cymru, and a few other companies have worked together to take down a DDoS botnet made up of Android devices.
The botnet — which researchers named WireX — appeared at the start of the month and was built using malware-infected apps distributed via third-party app stores and even the official Google Play Store.
Botnet discovered after noisy DDoS attacks
Evidence suggests that crooks began assembling their botnet in mid-July, but WireX came to the attention of security researchers on August 17, after its authors decided to use it to launch DDoS attacks.
Researchers say the attacks were quite powerful and managed to bring down various services. Some attacks came to the attention of law enforcement as attackers also sent ransom demands to the targeted organizations.
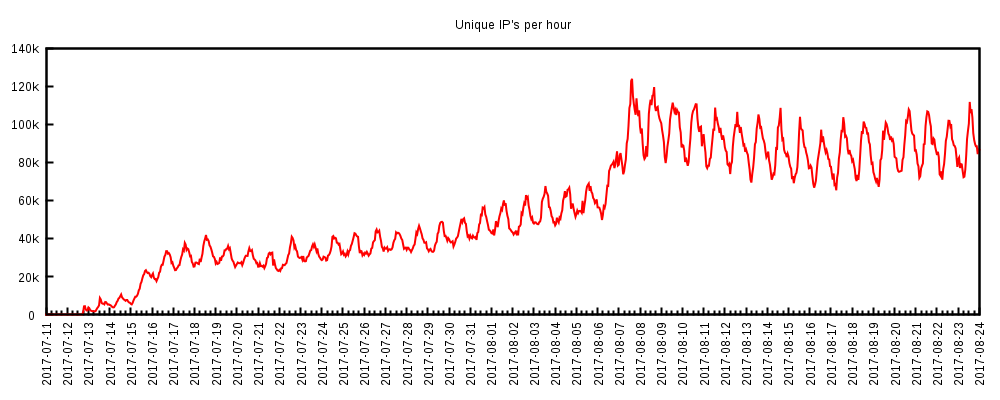
Data collected by various companies and aggregated for the purpose of identifying the source of these attacks reveals that in mid-August, the botnet was capable of launching DDoS attacks using bots spread across over 120,000 unique IP addresses.
It was because of this unique collaboration between competing companies that investigators managed to bring down the botnet so shortly after its creation.
WireX used to launch Layer 7 DDoS attacks
According to identical technical reports published online by the participants of this investigation [1, 2, 3, 4], WireX was capable of launching powerful Layer 7 (application-level) DDoS attacks that while they didn’t jam server bandwidth, they did exhaust server memory resources, causing online services to go down.
Experts say WireX was capable of launching a wave of HTTP GET and POST requests at targeted servers using user-agent strings resembling traffic coming from web browsers.
These user agent strings were in the form of random lowercase English alphabet characters.
User-Agent: jigpuzbcomkenhvladtwysqfxr
User-Agent: yudjmikcvzoqwsbflghtxpanre
User-Agent: fdmjczoeyarnuqkbgtlivsxhwp
User-Agent: yczfxlrenuqtwmavhojpigkdsb
User-Agent: dnlseufokcgvmajqzpbtrwyxih
User-Agent: mckvhaflwzbderiysoguxnqtpj
User-Agent: deogjvtynmcxzwfsbahirukqpl
WireX botnet created via malicious Android apps
Because security firms collaborated and pooled their data, they quickly identified all bots and discovered how victims got infected, tracking down over 300 Android apps containing the WireX malware.
Google intervened and removed the apps from the Play Store, and then used the tools at its disposal to remove the malicious apps from all infected devices.
Researchers say that current mobile antivirus solutions detect apps infected with the WireX malware as “Android Clicker.” This is because the malware also had the ability to perform click-fraud, which it used in the beginning, and then switched to launching DDoS attacks.
The trojan looks very similar to the GhostClicker malware previously analyzed by Trend Micro before its authors decided to use it to launch DDoS attacks.
Lessons learned from Mirai, WannaCry, NotPetya
Researchers who worked together on taking down the WireX threat said they decided to work together after seeing how quickly the united infosec community dealt with threats such as Mirai, WannaCry, and NotPetya in the last year.
Previous efforts to take down large-scale botnets, either be for DDoS attacks or financial fraud, have lingered for years and botnets survived multiple takedown attempts.

